Other HW Issues
Refresher Code Snippets
Python Flask
A minimal Flask server to demonstrate how to create an API endpoint.
from flask import Flask, jsonify
app = Flask(__name__)
@app.route('/api/data')
def get_data():
return jsonify({"message": "Hello, Flask!"})
if __name__ == '__main__':
app.run(debug=True)
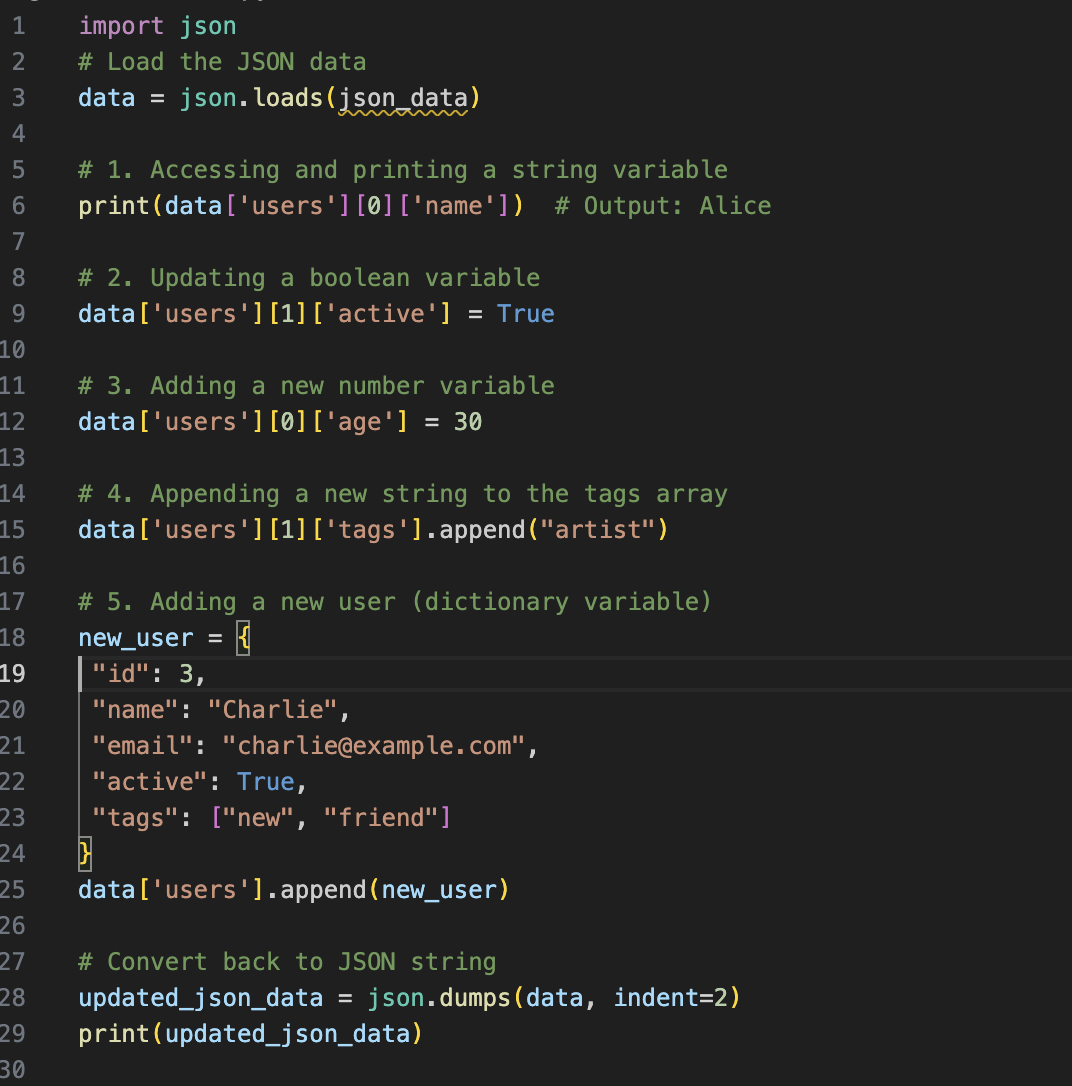
JSON Example
Demonstrating how to create and serialize JSON data in Python.
import json
data = {
"name": "Nathan",
"age": 15,
"hobbies": ["basketball", "badminton", "programming"]
}
json_string = json.dumps(data, indent=4)
print(json_string)
Simple Python Function
A function to perform arithmetic operations.
def calc_operations(num1, num2):
print(f"Addition: {num1 + num2}")
print(f"Subtraction: {num1 - num2}")
print(f"Multiplication: {num1 * num2}")
print(f"Division: {num1 / num2}")
calc_operations(10, 5)
Popcorn Hack - Find Students in a Score Range
Filtering a DataFrame based on a score range.
import pandas as pd
def find_students_in_range(df, min_score, max_score):
return df[(df['Score'] >= min_score) & (df['Score'] <= max_score)]
# Example DataFrame
data = {
"Name": ["Alice", "Bob", "Charlie"],
"Score": [85, 92, 78]
}
df = pd.DataFrame(data)
print(find_students_in_range(df, 80, 90))
Lists and Filtering
Some additional useful functions for working with data.
Find Students with Scores in a Range
def find_students_in_range(df, min_score, max_score):
filtered_df = df[(df['Score'] >= min_score) & (df['Score'] <= max_score)]
return filtered_df
Calculate Letter Grades
def add_letter_grades(df):
def score_to_letter(score):
if score >= 90:
return 'A'
elif score >= 80:
return 'B'
elif score >= 70:
return 'C'
elif score >= 60:
return 'D'
else:
return 'F'
result_df = df.copy()
result_df['Letter'] = result_df['Score'].apply(score_to_letter)
return result_df
Sequencing, Iteration, and Selection in Python
Sequencing
A simple sequence demonstrating data processing:
- Retrieve JSON data from a request.
- Check if the data is missing.
- Process the data and save it.
- Return success or error messages.
Iteration
recipes = {"Pasta": "Boil water, add pasta", "Salad": "Chop veggies, mix"}
for recipe_name, instructions in recipes.items():
print(f"{recipe_name}: {instructions}")
Selection
if not data:
return {"message": "No input data provided"}, 400
JavaScript Magic 8 Ball
A fun program simulating a Magic 8 Ball.
let facts = true;
console.log("Magic 8 Ball, does Nathan deserve an A in this class?");
console.log("[8] Magic 8 Ball is thinking ...");
console.log("[8] The ball has decided, that is " + facts);
Function to Save Recipe
This function sends recipe data to the backend:
async function saveRecipe(recipe) {
try {
const response = await fetch(`/save_recipe`, {
method: 'POST',
headers: {
'Content-Type': 'application/json'
},
body: JSON.stringify({
"name": recipe.dish,
"ingredients": recipe.ingredients,
"instructions": recipe.instructions
})
});
if (response.ok) {
alert('Recipe saved successfully!');
} else {
alert('Failed to save recipe.');
}
} catch (error) {
alert(`Error: ${error.message}`);
}
}
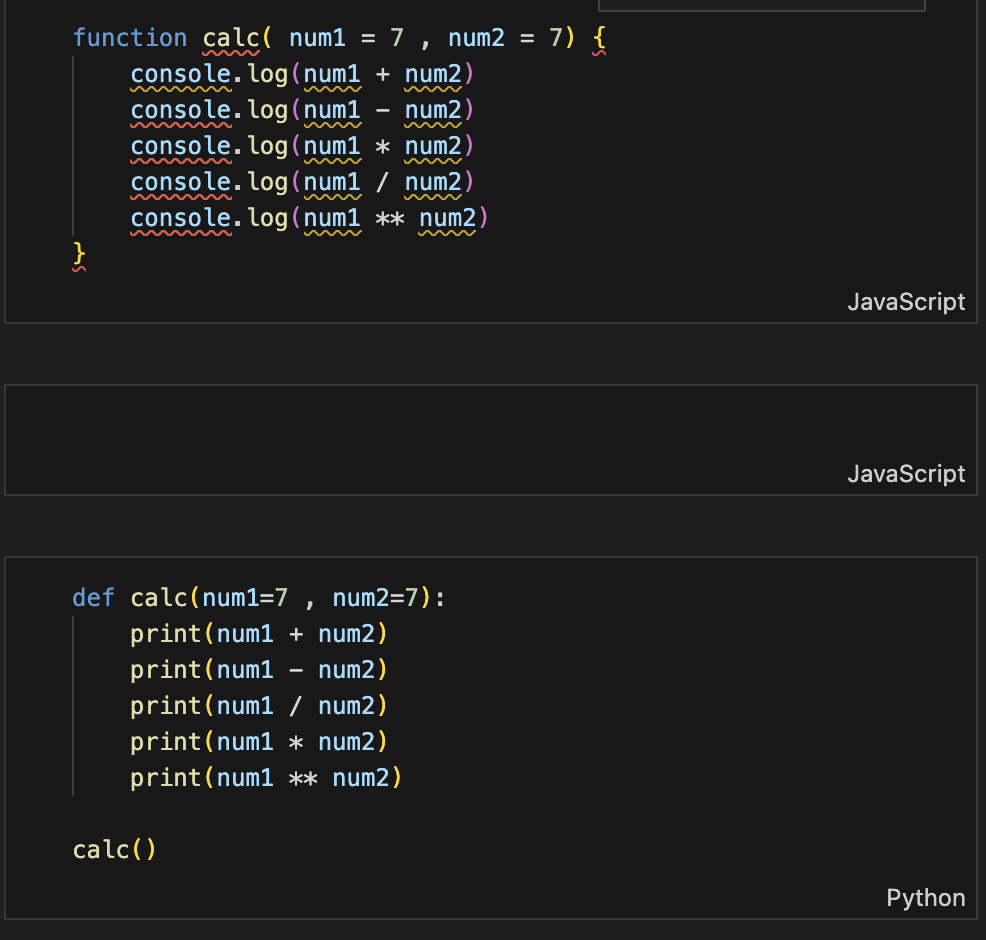
Arithmetic Operations in JavaScript
A function to perform arithmetic operations using JavaScript.
function calc(num1 = 7, num2 = 7) {
console.log(num1 + num2);
console.log(num1 - num2);
console.log(num1 * num2);
console.log(num1 / num2);
console.log(num1 ** num2);
}
Homeworks
3.1
The main thing that can be used to highlight the individuality of my presentation is the use of this name as the variable. The quizzes in this lesson also helped show me how to identify Python syntax errors.
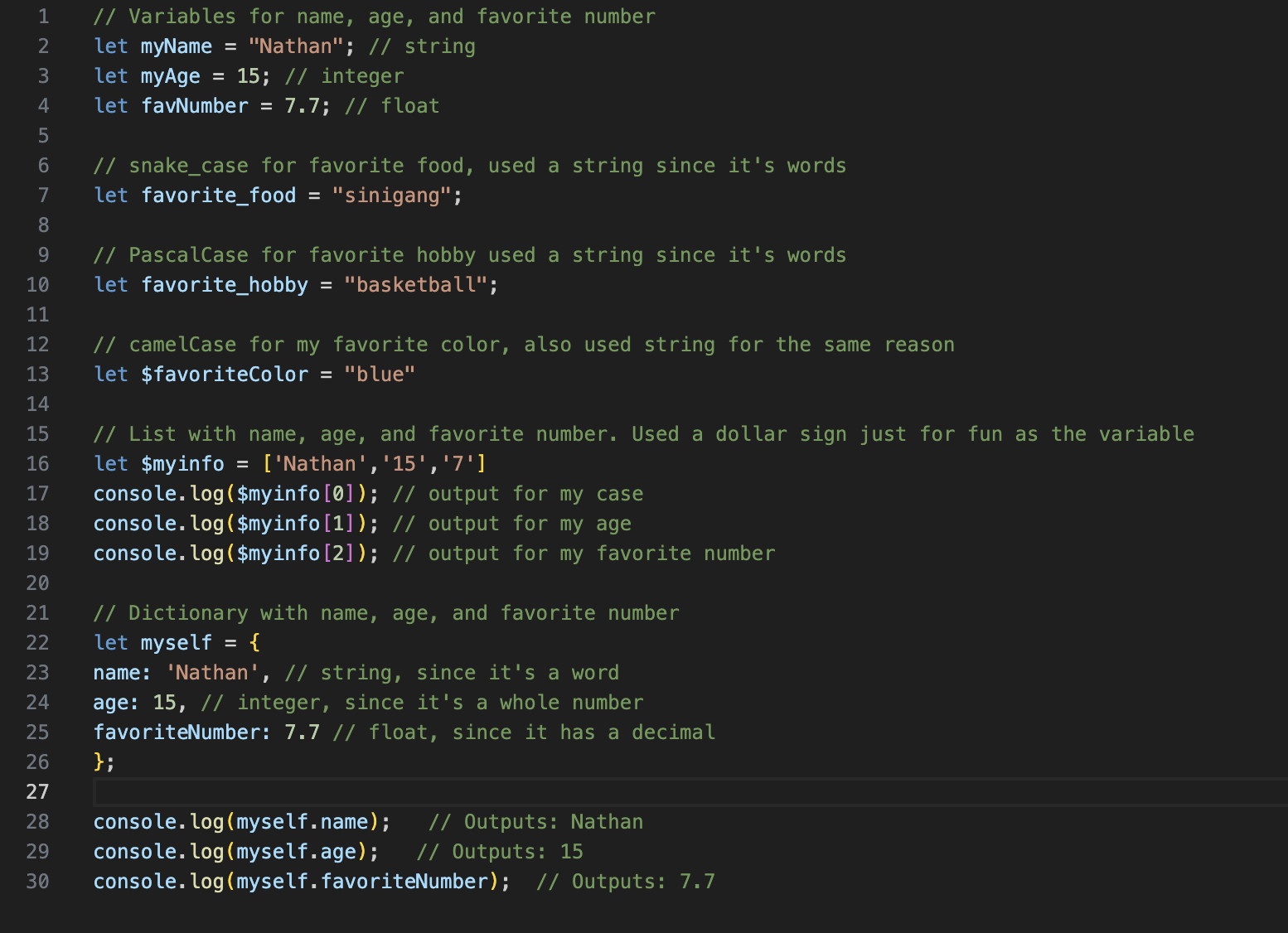
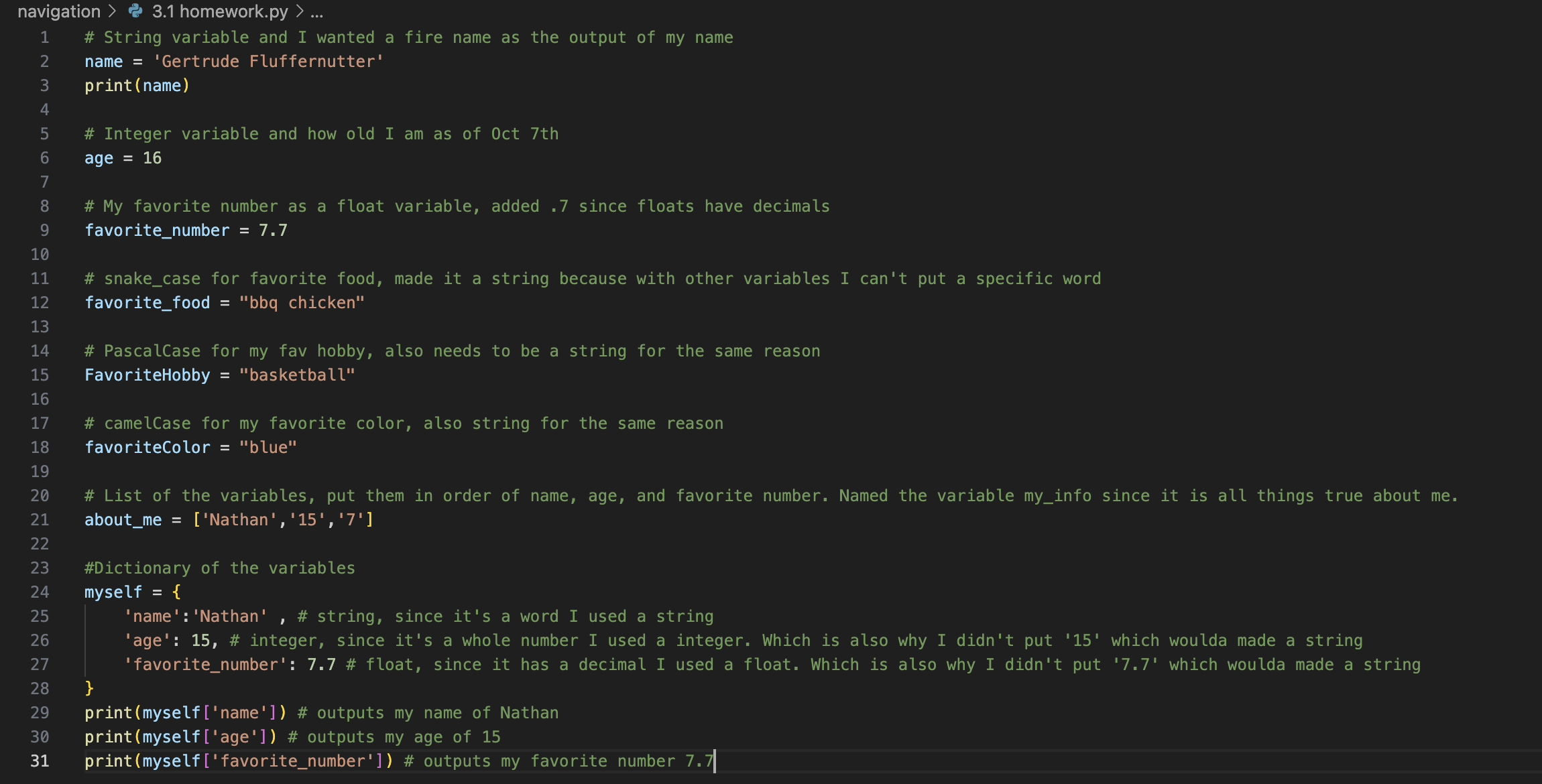
3.2
3.3
Here you can see that I started to indent better since in 3.1 I didn’t add many indents.
3.4

3.5
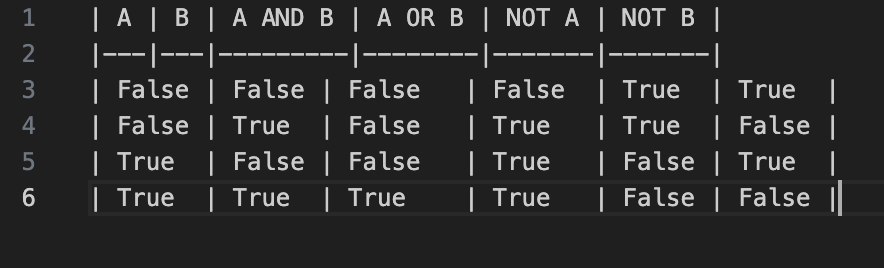
Goals:
- Learn what variables are
- Be able to identify different variables
- Get comfortable with
let,var, andconst - Learn about if statements and loops
Binary Search Techniques
Hack 1: Binary Search in Rotated Array
def binary_search_rotated(arr, target):
left = 0
right = len(arr) - 1
while left <= right:
mid = (left + right) // 2
if arr[mid] == target:
return mid
if arr[left] <= arr[mid]:
if arr[left] <= target < arr[mid]:
right = mid - 1
else:
left = mid + 1
else:
if arr[mid] < target <= arr[right]:
left = mid + 1
else:
right = mid - 1
return -1
arr = [4, 5, 6, 7, 0, 1, 2]
target = 1
print(binary_search_rotated(arr, target))
3.1 Homework - JavaScript Implementation
// Variables for name, age, and favorite number
let myName = "Nathan"; // string
let myAge = 15; // integer
let favNumber = 7.7; // float
// snake_case for favorite food
let favorite_food = "sinigang";
// PascalCase for favorite hobby
let favorite_hobby = "basketball";
// camelCase for my favorite color
let $favoriteColor = "blue";
// List with name, age, and favorite number
let $myinfo = ['Nathan','15','7'];
console.log($myinfo[0]); // Outputs: Nathan
console.log($myinfo[1]); // Outputs: 15
console.log($myinfo[2]); // Outputs: 7
// Dictionary with name, age, and favorite number
let myself = {
name: 'Nathan',
age: 15,
favoriteNumber: 7.7
};
console.log(myself.name); // Outputs: Nathan
console.log(myself.age); // Outputs: 15
console.log(myself.favoriteNumber); // Outputs: 7.7
Binary Search: Efficient Algorithms and Applications
Binary search is a powerful algorithm for finding an item in a sorted array with O(log n) time complexity. Below are three practical examples of binary search applications.
Hack 1: Binary Search in Rotated Array
This hack demonstrates how to apply binary search on a rotated sorted array to find a target value.
def binary_search_rotated(arr, target):
left = 0
right = len(arr) - 1
while left <= right:
mid = (left + right) // 2
if arr[mid] == target:
return mid
if arr[left] <= arr[mid]:
if arr[left] <= target < arr[mid]:
right = mid - 1
else:
left = mid + 1
else:
if arr[mid] < target <= arr[right]:
left = mid + 1
else:
right = mid - 1
return -1
# Example usage
arr = [4, 5, 6, 7, 0, 1, 2]
target = 1
print(binary_search_rotated(arr, target)) # Output: 5
Hack 2: Find First and Last Occurrence
This hack finds the first and last positions of a target value in a sorted array, which is useful for range queries.
def find_first_and_last(arr, target):
left = 0
right = len(arr) - 1
first = -1
while left <= right:
mid = (left + right) // 2
if arr[mid] == target:
first = mid
right = mid - 1
elif arr[mid] < target:
left = mid + 1
else:
right = mid - 1
left = 0
right = len(arr) - 1
last = -1
while left <= right:
mid = (left + right) // 2
if arr[mid] == target:
last = mid
left = mid + 1
elif arr[mid] < target:
left = mid + 1
else:
right = mid - 1
if first == -1:
return -1
return (first, last)
# Example usage
arr = [1, 2, 2, 2, 3, 4, 5]
target = 2
print(find_first_and_last(arr, target)) # Output: (1, 3)
Hack 3: Smallest Element Greater or Equal to Target
This hack finds the smallest element in a sorted array that is greater than or equal to a target value.
def search_smallest_greater_or_equal(arr, target):
left = 0
right = len(arr) - 1
result = -1
while left <= right:
mid = (left + right) // 2
if arr[mid] >= target:
result = arr[mid]
right = mid - 1
else:
left = mid + 1
return result
# Example usage
arr = [1, 3, 5, 7, 9, 11]
target = 8
print(search_smallest_greater_or_equal(arr, target)) # Output: 9
MCQ’s Strengths and Weaknesses (Collective of All MCQ’s)
✅ Strengths:
- Conditionals, developing procedures, data compression, iteration.
❌ Weaknesses:
- Strings, binary search, boolean expressions,
Accomplishments:
- Basic static recipes for users added for the main function of the websites random recipes.
- Learning what the messages in postman mean ex: 404, 200, 201, and 500.
- Learn mathematical operators and how to use them
- Learn about JavaScript Object Notation (JSON)
Big Ideas
1.1 Program Design
- Purpose: Understanding the goals behind a program.
- Design: Crafting algorithms, flowcharts, and pseudocode for planning.
- Incremental Development: Building and testing programs in manageable chunks.
- Collaboration: Utilizing version control systems (Git) and pair programming.
- Documentation: Writing code that’s easy to follow, with appropriate comments.
1.2 Program Abstraction
- Procedural Abstraction: Designing functions and procedures to organize code.
- Data Abstraction: Working with variables, data structures, and APIs to manage complexity.
- Abstraction Levels: Moving from high-level programming concepts to low-level binary.
- Hiding Implementation: Creating clear and simple interfaces and APIs.
- Parameters and Return Values: Passing information into and out of functions.
1.3 Program Implementation
- Problem-Solving: Breaking down larger problems into simpler tasks.
- Algorithm Design: Structuring step-by-step solutions to problems.
- Programming Features: Using variables, control structures, and functions.
- Libraries/APIs: Leveraging existing tools and frameworks to streamline development.
- Testing: Validating program functionality and ensuring it meets requirements.
1.4 Identifying and Correcting Errors
- Types of Errors: Syntax, logic, and runtime issues.
- Debugging: Using tools like print statements, debuggers, and tracing to locate bugs.
- Testing Strategies: Testing boundary cases, edge cases, and typical scenarios.
- Error Handling: Implementing error messages and handling exceptions using try/catch.
- Code Review: Collaborating with others to find and fix bugs.
2.1 Binary Data Representation
- Binary Representation: The method of expressing decimal numbers as binary.
- Bits and Bytes: Understanding how basic data is stored in the form of bits and bytes.
- Conversions: Techniques for converting between decimal, binary, and hexadecimal systems.
- Integer vs. Real Numbers: How computers handle fixed-point numbers (integers) and floating-point numbers (real numbers).
- Limitations: Challenges associated with numeric representations, including overflow.
2.2 Data Compression
- Lossless Compression: Algorithms that compress data without any loss of information.
- Lossy Compression: Compression methods that reduce file size by discarding some data, which can affect quality.
- Common Formats: Frequently used compression formats include JPEG (for images), MP3 (for audio), and ZIP (for files).
- Run-Length Encoding: A simple method of compression where sequences of the same value are stored as a single value and count.
- Huffman Coding: A more advanced compression method based on the frequency of data elements.
2.3 Extracting Information from Data
- Data Collection: Different methods used to gather raw data.
- Data Analysis: Techniques that help interpret and derive meaningful insights from data.
- Visualization Tools: Tools like charts and graphs used to make data easier to understand.
- Metadata: The “data about data” that helps explain the context or additional details of the primary data.
- Drawing Conclusions: Making informed decisions or observations based on data analysis.
2.4 Using Programs with Data
- Data Processing: The transformation or manipulation of data to make it more useful or readable.
- Data Filtering: The process of extracting relevant data from a larger dataset.
- Searching Algorithms: Techniques used to locate specific pieces of data within a dataset.
- Sorting Algorithms: Methods for organizing data into a structured order.
- Data Storage: Systems and techniques for saving data, such as databases and file systems.
2.5 Big Data
- Characteristics: Big Data is often defined by the 4 V’s: volume, velocity, variety, and veracity.
- Benefits: Big Data can uncover patterns, trends, and insights that can be used for predictions.
- Challenges: Managing Big Data includes concerns about storage, processing, and privacy.
- Technologies: Technologies like Hadoop, MapReduce, and cloud computing help in processing large datasets.
- Ethical Considerations: The ethical issues related to Big Data include biases in data, privacy concerns, and security risks.
3.1 Variables and Assignments
- Types of Variables: Numeric, string, and boolean types.
- Assignment Operations: Setting and modifying the value of variables.
- Constants: Variables that retain fixed values throughout the program.
- Naming Guidelines: Best practices for choosing clear and meaningful variable names.
- Scope: The difference between global and local variables.
3.2 Data Structures
- Lists/Arrays: Collections of ordered elements.
- Dictionaries/Maps: Key-value paired data structures.
- Sets: Unordered collections with unique elements.
- Objects: Custom-built data structures.
- Nested Structures: Lists within lists or other complex structures.
3.3 Mathematical Expressions
- Arithmetic Operations: Basic operations like addition (+), subtraction (-), multiplication (*), division (/), and modulus (%).
- Assignment Operations: The use of =, +=, and -= to change variable values.
- Order of Operations: Understanding the rules of PEMDAS in programming.
- Rounding and Truncation: Handling decimal numbers and reducing precision.
- Mathematical Libraries: Using built-in functions to perform advanced math operations.
3.4 Strings
- String Operations: Combining strings, extracting substrings, and more.
- String Methods: Using functions like length, find, and replace.
- String Formatting: Formatting text to display output neatly.
- Character Access: Using indices to access individual characters in strings.
- String Immutability: Understanding that strings cannot be changed once created.
3.5 Boolean Expressions
- Logical Operations: Using AND, OR, and NOT to combine boolean expressions.
- Comparison Operations: Checking equality (==), inequality (!=), greater than (>), less than (<), etc.
- Truth Tables: Visualizing all possible outcomes of boolean expressions.
- Short-Circuit Evaluation: How boolean expressions can be evaluated early to improve performance.
- DeMorgan’s Laws: Techniques for simplifying boolean expressions.
3.6 Conditionals
- If Statements: Using conditions to select between two options.
- If-Else Statements: Introducing a second option when the condition is not met.
- If-Elif-Else Statements: Handling multiple conditions in a clear structure.
- Nested Conditionals: Embedding conditional statements within each other.
- Switch/Case Statements: An alternative to using multiple if statements.
3.7 Nested Conditionals
- Structure: Organizing if statements in a nested fashion.
- Complexity Management: Keeping nested conditions understandable.
- Boolean Algebra: Simplifying and organizing conditions using boolean logic.
- Nesting Approaches: Various styles and practices for effective nesting.
- Decision Trees: Using nested conditions for building complex decision logic.
3.8 Iteration
- For Loops: Iterating through a block of code a specific number of times.
- While Loops: Repeating a block of code while a condition holds true.
- Nested Loops: Using one loop inside another for more complex tasks.
- Loop Control: Breaking out of loops or skipping to the next iteration using break and continue.
- Infinite Loops: How to avoid or handle loops that run indefinitely.
3.9 Developing Algorithms
- Algorithm Basics: Step-by-step procedures for solving problems.
- Designing Algorithms: Planning out solutions before writing code.
- Pseudocode: Writing algorithm steps in human-readable form.
- Flowcharts: Creating visual representations of algorithm logic.
- Algorithm Evaluation: Assessing the efficiency of algorithms.
3.10 Lists
- Creating Lists: Initializing and populating lists.
- List Operations: Accessing, adding, and removing elements.
- List Methods: Using common techniques to modify lists.
- List Traversal: Iterating through a list to process each element.
- 2D Lists: Working with list data organized in rows and columns.
3.11 Binary Search
- Binary Search Algorithm: The process of finding an element in a sorted list.
- Requirements: The list must be sorted for binary search to work.
- Implementation: Writing the code for binary search.
- Time Complexity: Binary search operates in O(log n) time, making it efficient.
- Use Cases: Scenarios where binary search is preferred for efficiency.
3.12 Calling Procedures
- Procedure Definition: Writing reusable blocks of code.
- Passing Parameters: Sending data to procedures for processing.
- Return Values: Getting results from procedures after execution.
- Procedure Invocation: Calling procedures in your program.
- Stack Frames: Understanding how procedures are executed in memory.
3.13 Developing Procedures
- Procedural Abstraction: Breaking down code into reusable procedures.
- Parameters and Return Types: Designing procedures with proper interfaces.
- Documentation: Writing descriptions for each procedure for clarity.
- Testing Procedures: Ensuring procedures behave as expected.
- Procedure Libraries: Creating a set of reusable procedures for future use.
3.14 Libraries
- Standard Libraries: Using built-in libraries that come with the programming language.
- Third-Party Libraries: Installing and using external libraries.
- API Documentation: Reading and understanding documentation to use libraries effectively.
- Installing Libraries: Adding third-party libraries to my projects.
- Using Libraries: Importing and utilizing library functions in my code.
3.15 Random Values
- Random Number Generation: Creating random values for various purposes.
- Seeding Randomness: Controlling the randomness for repeatable results.
- Range Selection: Generating random values within specified ranges.
- Applications: Using randomness in games, simulations, and encryption.
- Pseudorandom vs. True Random: The difference between pseudo-random numbers generated by algorithms and true random values.
3.16 Simulations
- What is a Simulation?: Modeling real-world phenomena or systems with code.
- Monte Carlo Methods: Using randomness in simulations to estimate solutions.
- Designing Simulations: Planning and building realistic simulation models.
- Data Collection: Gathering data from simulations to analyze results.
- Analyzing Results: Interpreting data from simulations to draw conclusions.
3.17 Algorithm Efficiency
- Time Complexity: How the time required to run an algorithm increases with input size.
- Space Complexity: How much memory an algorithm uses relative to the input size.
- Big O Notation: Notation used to describe the upper bound of an algorithm’s complexity.
- Choosing Algorithms: Evaluating algorithms based on efficiency.
- Optimization: Improving algorithms to run faster or use less memory.
3.18 Undecidable Problems
- The Halting Problem: An example of a problem that is undecidable by a computer.
- Computational Limits: Understanding the types of problems that computers cannot solve.
- P, NP, and NP-Complete: Classifying problems based on their difficulty.
- Heuristics: Using approximations for problems that can’t be solved exactly.
- Real-World Implications: Examples of undecidable problems in practical computing.
4.1 The Internet
- Internet Structure: Components like routers, switches, and servers.
- Protocols: Key protocols such as HTTP, HTTPS, FTP, and SMTP.
- IP Addressing: The differences between IPv4, IPv6, and the role of DHCP.
- DNS (Domain Name System): The process of translating domain names into IP addresses.
- ISPs (Internet Service Providers): Companies that provide internet connectivity.
4.2 Fault Tolerance
- Redundancy: The practice of having backup systems and components.
- Error Detection: Methods like checksums and error codes to identify issues.
- Error Correction: Techniques used to automatically fix errors in data transmission.
- Failover Systems: Systems that automatically switch to a backup in case of failure.
- Distributed Systems: Techniques that distribute tasks across multiple systems to reduce risk.
4.3 Parallel and Distributed Computing
- Parallel Processing: Using multiple cores or processors to speed up computation.
- Distributed Computing: Spreading tasks across multiple computers in a network.
- Load Balancing: Efficiently distributing work across servers to prevent overloads.
- MapReduce: A framework for processing large data sets in parallel.
- Cloud Computing: Utilizing remote servers over the internet to store, manage, and process data.
4.4 Computer Components
- CPU (Central Processing Unit): The brain of the computer responsible for executing instructions.
- Memory (RAM): Temporary storage for data that is being actively used.
- Storage: Long-term data storage devices like hard drives and SSDs.
- Input/Output Devices: Devices for user interaction like keyboards, mice, and monitors.
- Motherboard: The primary circuit board that connects all computer components.
4.5 Operating Systems
- Operating System Functions: Managing resources and providing user interfaces.
- Process Management: Running and managing multiple applications simultaneously.
- Memory Management: Allocating and protecting memory resources.
- File Systems: Organizing and storing data efficiently.
- User Interfaces: Differentiating between command line and graphical user interfaces.
4.6 Networks
- Network Types: Differences between LAN, WAN, PAN, and MAN.
- Network Topologies: Different ways to organize network nodes: star, bus, mesh, and ring.
- Network Devices: Devices like routers, switches, and access points that enable network connectivity.
- Bandwidth and Latency: Metrics used to measure network performance.
- Wireless vs. Wired Connections: Comparing the pros and cons of each connection type.
4.7 Network Security
- Threats: Common security risks including malware, phishing, and DDoS attacks.
- Encryption: The use of cryptography to secure data during transmission.
- Authentication: Verifying the identity of users or systems.
- Authorization: Managing user permissions to access specific resources.
- Firewalls and Security Software: Tools used to protect networks and devices from threats.
5.1 Beneficial and Harmful Effects
- Positive Impact: Increased efficiency, better connectivity, and innovation.
- Negative Impact: Privacy risks, job loss, and technology addiction.
- Unforeseen Outcomes: Unpredictable consequences of technology use.
- Weighing Benefits and Risks: Ethical decision-making in tech development.
- Real-world Examples: Case studies of both positive and negative computing impacts.
5.2 Digital Divide
- Definition: Unequal access to technology and tech literacy.
- Root Causes: Economic disparities, geographic location, and lack of education.
- Global Differences: The digital divide’s effects across various countries.
- Addressing Inequality: Programs designed to bridge the gap.
- Future Developments: How the digital divide may evolve.
5.3 Computing Bias
- Algorithm Bias: Unfair or discriminatory results from algorithms.
- Data Bias: Bias present in training data used to build systems.
- Design Bias: Biases that stem from user interface design choices.
- Impact on Society: How bias in computing affects different groups.
- Reducing Bias: Strategies for mitigating or eliminating bias in computing.
5.4 Crowdsourcing
- Definition: Collecting input from a large group of individuals.
- Uses: Examples include platforms like Wikipedia and open-source projects.
- Advantages: Access to a variety of viewpoints and large-scale collaboration.
- Challenges: Ensuring quality and managing coordination.
- Crowdsourcing Tools: Platforms and tools that enable crowdsourcing.
5.5 Legal and Ethical Concerns
- Intellectual Property: Protecting creations through copyright, patents, and trademarks.
- Licensing: The difference between open-source and proprietary software.
- Privacy Legislation: Laws like GDPR, CCPA, and HIPAA that protect user data.
- Ethical Principles: Different approaches to ethics in technology.
- Tech Professional Ethics: The ethical responsibilities of those in the tech industry.
5.6 Safe Computing
- Personal Security: Using strong passwords and enabling two-factor authentication.
- Data Protection: Implementing encryption and maintaining backups.
- Physical Safety: Ergonomics and managing screen time to avoid physical strain.
- Recognizing Threats: Identifying phishing attempts and social engineering tactics.
- Balancing Security: Finding the right balance between convenience and safety.
Binary Search Algorithm
- Definition: A search algorithm that finds the position of a target value within a sorted list by repeatedly dividing the search interval in half.
- Time Complexity: O(log n), making it much faster than linear search for large datasets.
- Requirements: The data must be sorted.
- Steps:
- Compare the target value to the middle element of the list.
- If they match, return the middle element’s index.
- If the target is smaller, repeat the process for the left half.
- If the target is larger, repeat the process for the right half.
- Use Cases: Efficient for searching in large sorted datasets like dictionaries or databases.
Lists and Filtering Algorithm
- Definition: Lists store an ordered collection of items, and filtering algorithms are used to select a subset of data based on a condition.
- Common Operations: Accessing, adding, removing, and modifying elements.
- Filtering: Removing elements that don’t meet a certain condition (e.g., filtering out even numbers or specific categories).
- Time Complexity: O(n), where n is the number of elements in the list.
- Use Cases: Data processing, user input validation, and selecting relevant data from large datasets.
Simulation Games / Random Algorithms
- Definition: Simulation games and random algorithms use randomness to model real-world processes or create unpredictable behaviors in games.
- Simulation: A model that mimics a real-world process or system.
- Random Algorithms: Algorithms that introduce random decisions or outputs (e.g., random number generation).
- Monte Carlo Methods: A method for solving problems using repeated random sampling to estimate results.
- Use Cases: Game development (random events), financial modeling, scientific simulations.
Big O and Algorithm Efficiency
- Big O Notation: Describes the upper bound of an algorithm’s growth rate as the input size increases.
- Time Complexity: How the runtime of an algorithm increases with input size.
- Space Complexity: How the memory requirements grow with input size.
- Common Big O Notations:
- O(1): Constant time, unaffected by input size.
- O(n): Linear time, where performance grows linearly with input size.
- O(log n): Logarithmic time, common in algorithms like binary search.
- O(n²): Quadratic time, common in algorithms like bubble sort.
- Use Cases: Optimizing algorithms for performance, comparing different algorithms for efficiency.
Undecidables and Heuristics
- Undecidable Problems: Problems for which no algorithm can always provide an answer in a finite amount of time (e.g., the halting problem).
- Heuristics: Problem-solving strategies or “rules of thumb” that help find good enough solutions when exact solutions are not feasible.
- Halting Problem: A problem that asks whether a given program will terminate or run indefinitely. It is undecidable.
- P vs. NP: The question of whether every problem whose solution can be verified quickly (NP) can also be solved quickly (P).
- Heuristic Methods: Used to find approximate solutions when an exact solution is impossible or impractical.
- Use Cases: AI search algorithms (e.g., A*), real-world optimization problems where perfect solutions are computationally impossible.
Two-Week Python and Web Development Study Plan
Week 1: Python Fundamentals & Flask
- Variables and Data Types
- Master different variable types (strings, integers, floats)
- Practice JSON handling with the
jsonmodule - Complete the arithmetic operations exercise from my blog
- Control Flow and Functions
- Review if-else statements and conditionals
- Build custom functions like
calc_operations - Practice Python function parameter passing
- Data Structures
- Focus on lists and dictionaries
- Implement pandas DataFrame filtering with
find_students_in_range -
Practice letter grade calculations with the
add_letter_gradesfunction - Flask Web Development
- Set up a basic Flask server following my example
- Create JSON API endpoints
-
Implement a recipe saving feature with my
saveRecipeJavaScript function - Iteration and Simulation
- Practice different loop structures in Python
- Implement a simple Monte Carlo simulation
- Create a random-based game using concepts from my Magic 8 Ball example
Week 2: JavaScript & Data Processing
- JavaScript Fundamentals
- Review JavaScript variable declarations and operations
- Practice DOM manipulation and event handling
-
Work with JavaScript functions and parameters
- Algorithm Practice
- Compare algorithm efficiency using Big O notation
- Implement binary search for a real-world problem
-
Practice data filtering techniques from my notes
- JavaScript Game Mini-Project
- Build a simple browser-based game that:
- Uses basic JavaScript and HTML
- Implements the Magic 8 Ball concept from my blog
- Allows user interaction through buttons and text input